

Currently, the threat of attacks and hacks of websites of both large and small companies is growing.
On May 26, 2023, a mass defacement of web servers of the Russian national segment of the Internet was carried out. The target of the attack was the Bitrix CMS. During the investigation, it was established that mass hacks were carried out in advance, starting in 2022, through known vulnerabilities, including CVE-2022-27228. The attacker installed a backdoor that allows creating arbitrary files and calling OS commands. On May 26 at around 14:00, the backdoor was given a command to replace the main page of the site. The technical description of the attack was published on the developers' forum (Topic from 06/28/2022 "Websites hacked in honor of the Ukrainian Constitution Day" is updated with new cases of hacking).
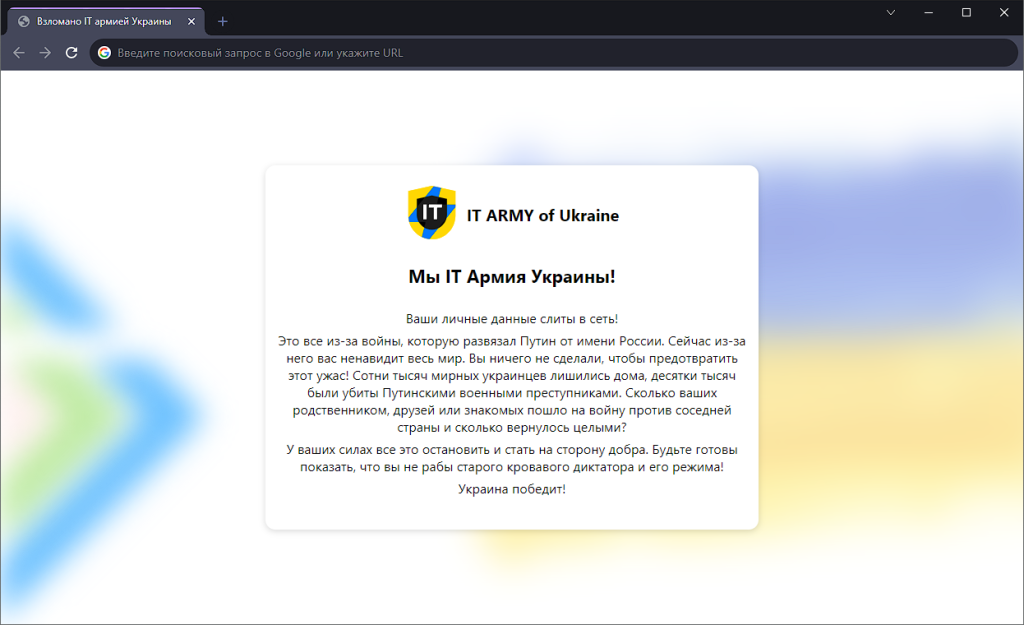
Example of a hacked site, source: telegra.ph/hck-bx-0526-05-26
Some web projects use CMS «1C-Bitrix». Some use solutions from other vendors. Some are self-written sites.
The exact reason for the hacking and the software through which the hackers entered are unknown. It is important to understand that the situation does not depend on a specific vendor and its software.
The entry point can be unupdated: CMS, e-commerce platform, PHP versions, databases and other server software. But! An emergency update is not enough.
Hackers could install bookmarks and Trojans at any time while you were using outdated software. And activate them months and years later. The site can be hacked without any external signs.
According to the company "1C-Bitrix", hacked projects on "1C-Bitrix" have not been updated for a long time. Or they were updated irregularly. 1C-Bitrix is closely monitoring the situation and has prepared key recommendations:
Install the latest updates to the CMS and any other software from the critical infrastructure of your site.
Perform a security audit of the entire software complex associated with the site. There are many ways to hack a web project.
Contact the vendor's technical support. Regardless of the activity of your license. If your license level includes 24/7 calls, use them to speed up the process.
Self-written code is a potential hacking threat. Be sure to check all elements with "manual assembly". Attacks and infections can start from there.
Bring the site into compliance with the recommendations from the CyberOK team. If you follow them, the risk of hacking is minimal.
Hacked sites are often restored from a backup copy, but this does not solve the problem, since the backdoor is also restored, which allows the attacker to repeat the attack. In addition, if the vulnerability has not been eliminated, attackers can hack the server again and install a modification of the backdoor, which is currently observed.
The attackers' targets are:
● All non-updated versions of "1C-Bitrix: Site Management" (Bitrix Site Manager). Please note that after the license expires, the software is not updated.
● Updated versions of "1C-Bitrix: Site Management" with unpatched vulnerabilities.
● Updated versions of "1C-Bitrix: Site Management" with an installed backdoor.
The company Tonweb Agency has been dealing with information security issues of web projects since 2016. Currently, we use the regulations "Recommendations for the application of compensatory measures and response to attacks related to the CMS "1C-Bitrix: Site Management"" dated 01.06.2023 together with previously acquired experience, namely:
1) Containment (if it is impossible to update the CMS);
2) Carrying out preventive measures;
3) For third-party and/or unprotected projects, we successfully (but labor-intensively) apply response measures to a successful attack.
● Translation of the site to the current version of PHP 8;
● Installation, activation and configuration according to the recommendations of the modules:
o «Proactive filter (Web Application Firewall)»
o «Activity control»;
● Performing a check of the WEB application using the «Security Scanner»;
● Closing access to some files at the server level;
● Checking and enabling logging of WEB application access events (all types of access) and errors (error);
● Updating server software.
List of works for weekly updating of "1C-Bitrix: Site Management" to current versions:
1) Deploying the project on a test server;
2) Installing CMS and module updates;
3) Comprehensive (automated and manual) testing and, if necessary, adjusting the integration of the site with the CMS after the update, making adjustments to the integration in a separate branch for further automated transfer to the main branch (using VCS), as well as testing the project after making such adjustments;
4) Transferring changes to the main server and transferring integration adjustments, final testing.

In some cases, the site may be blocked by the NKTsKI due to its hacking with subsequent posting of illegal content and use by intruders to carry out computer attacks on the critical information infrastructure of the Russian Federation in accordance with Article 5 of Federal Law No. 187-FZ "On the Security of the Critical Information Infrastructure of the Russian Federation", paragraph 5.1 of the Order of the FSB of Russia dated July 24, 2018 No. 366 and paragraph 9 of the Rules for the Centralized Management of the Public Communications Network, approved by the Decree of the Government of the Russian Federation dated February 12, 2020 year No. 127. Blocking is applied until the NKTsKI records the fact of removal of illegal content.
In this case, after eliminating the defacement, backdoor and vulnerabilities, we transfer the information to the team of the National Coordination Center for Computer Incidents.
Roskomnadzor blocks the site the next day after sending the notification, and the issue of unblocking is considered within 30 days (during this time, the site may completely disappear from the index of search engines, which will reduce the result of the work of SEO specialists to zero), so it is critically important to prevent blocking of your site.
By continuing to use this site, you agree to the use of cookies in accordance with policy privacy.